You might be exposed to cyber hacking activities if you are using The Indian Overseas Bank App, finds Appvigil
Indian Overseas Bank (IOB) is a major bank in India with about 3350 domestic branches and eight branches and offices overseas. The net profit for the quarter ended 30 June 2014 stood at INR 272 Crores. The Business touched INR 4,20,739 Crores (YoY Growth 8.16%) for the quarter ended 30 September 2014. The Indian Overseas Bank Android app has 50,000 to 1,00,000 downloads on Google Play. Appvigil, a cloud based android app security scanner discovered a JavaScript Injection vulnerability also known as cross-scripting or XSS vulnerability in the Indian Overseas Bank Android app.
The report clearly listed all the vulnerabilities along with the activities in which they were present. Based on the same, AppVigil decided to conduct a small experiment on the android application of ‘Indian Overseas Bank’. They launched the application in an emulated local environment, accessing the WebView of the application and executed some JavaScript code in WebView that dynamically changed the ‘About Us’ page to a Login page. After this, a username and password were logged in which was accessible from outside the android application.
This vulnerability will become really dangerous for IOB android app users if a fully permitted malware performs this attack on the app in the same device and steals users’ netbanking usernames & passwords.
https://www.youtube.com/watch?v=yhm0VN98gZk
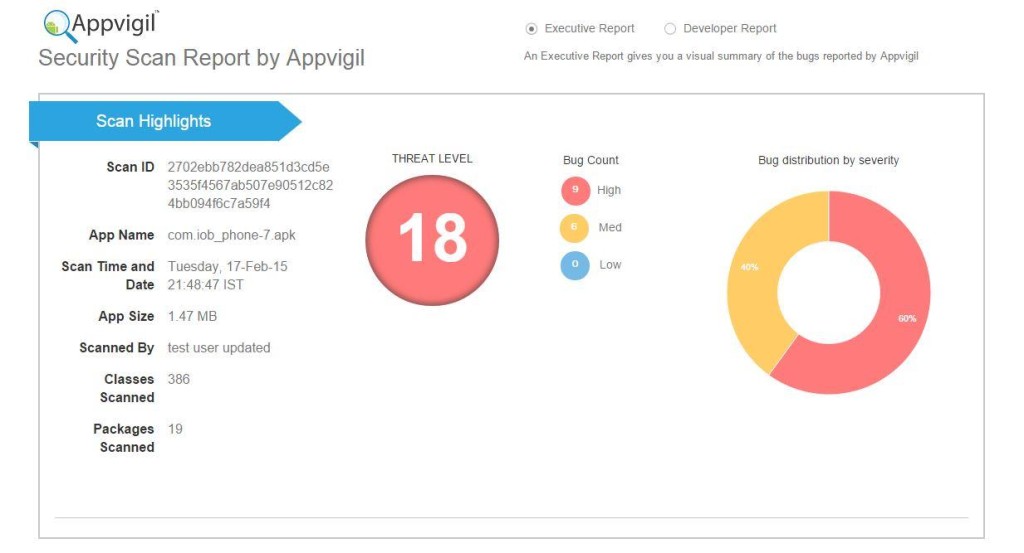
Security Report
About the vulnerability
Java script injected in activity: com.iob_phone.ui.IOBProductDetailActivitywith injection String: document.getElementsByTagName(‘body’)[0].setAttribute(‘style’, ‘background-color: red’);
Severity and Impact
Local HTML modifications via malware or other apps results in execution of malicious JavaScript in the presentation layer of the app. This may result in information theft.
It should be verified that JavaScript and Plugin support is disabled for any WebViews (usually default).
It has to be ensured that all UIWebView calls don’t get executed without proper input validation. Apply filters for dangerous JavaScript characters if possible, using a whitelist over blacklist character policy before rendering.
In today’s agile development environment, about 70-80% of all android apps are hackable, as developers focus more on productivity and innovation, pushing their security concerns backstage. With the amount of information, the android apps ask for and consume, it is only logical that these applications appear as a very lucrative and attractive target for hackers. This is where Appvigil comes in.
Appvigil provides an automated test framework for android developers to scan and test their android applications against state of the art security vulnerabilities. The developers can use Appvigil to scan their application executables for a detailed report containing the type of vulnerability, exact location of the security concern in the application and references/guide to patch up the security issues in their android apps.
About Wegilant
Wegilant is an emerging cloud based mobile app security company. Their flagship product is Appvigil, which is a cloud based android app security scanner. Appvigil looks for security vulnerabilities and loopholes in android apps and helps you identify whether an android app is hackable or not. Wegilant is incubated in Society for innovation and entrepreneurship (SINE), IIT Bombay. Wegilant is one the Top 10 Emerging Software Product Centric Companies for F. Y. 2014 as per NASSCOM.